Cisco provides several Layer 2 security technologies to secure the network infrastructure against various types of attacks. These include Spanning Tree Protocol (STP) security, port security, and VLAN Access Control List (VACL) security. In summary, Cisco provides several Layer 2 security technologies, such as STP security, port security, and VACL security, which can be used …
Category: Gigabit Ethernet Design Rules
Jul 20
Best Practices for Hierarchical Layers – Advanced Enterprise Campus Design
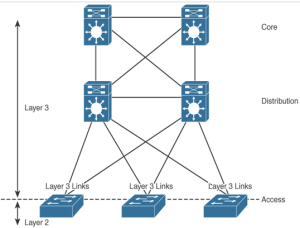
Each layer of the hierarchical architecture requires special considerations. The following sections describe best practices for each of the three layers of the hierarchical architecture: access, distribution, and core. Access Layer Best Practices When designing the building access layer, you must consider the number of users or ports required to size up the LAN switch. …
May 15
Hybrid Access Layer – Advanced Enterprise Campus Design
The hybrid access layer combines the use of Layer 2 switching with Layer 3 at the access layer. In this design, some VLANs are defined in the access layer and others in the distribution layer. There are Layer 3 and Layer 2 links between the distribution switches and the access switches. With the Layer 2 …
- 1
- 2